Computer Software
Development Software
What is it? Software with the purpose of allowing users to create or fix pieces of code
3 Main Types
Integrated Development Environment (IDE): Allows one to write code, as well as, interpret and execute the commands being written one by one. An IDE can also debug and find problems in the written code.
Compiler: Allows for code to be translated from one language into another language that the computer understands. This results in a file ready to be executed, however, a compiler does not execute commands
Interpreter: Interprets a program one line at a time and executes the commands as it arrives
Malware
Any piece of software that is disruptive and
has malicious intent
5 General Categories
Viruses: Spreads by copying its self and can affect computers functionality by changing programs
Trojan Horse: A program or file
that is not what it says it is
SpyEye would secretly implant itself
onto people's computers to steal their
personal and financial information
Adware/Spyware: Collects information
about the user and changes web
searches to other sites

Fireball turns default web browsers to fake search engines, which enable the software to spy on users of the infected browsers
Worm: Is like a virus, however
does not need to change exist-
ting programs to work

SQL Slammer was a Denial of Service on many internet hosts that caused thousands of network outages and slowed down Internet traffic
Backdoor: Anyway around
security measures without
authority

ShadowPad extracts information about the host, executes commands, interacts with the file system and registry, and deploys new modules to extend functionality.
Time Line of Viruses
5 Ways to Prevent Viruses
Install antivirus or Anti-malware Software
Don't Use Unsecure WiFi
Back Up Files
Ideally you should keep your important files in 3 different locations including hardware, so that if one is attacked your files are not lost
Use Secure Passwords
If you always use the same password and someone uncovers it, it’ll take just a few seconds to hack into all your accounts. Choose a strong password with lower- and upper-case letters, numbers and symbols
Be Careful of What You Open
Many viruses are spread when one opens suspicious emails, etc. Insure to avoid websites you don't know, emails from sketchy companies, and think before downloading
Application Software
4 Categories
Productivity: Software with the purpose to assist
users with paperwork and editing

Excel

Access
Photoshop

Microsoft Word
Entertainment: Simple software made to
entertain the general audience of users

Undertale
Spotify

Netflix
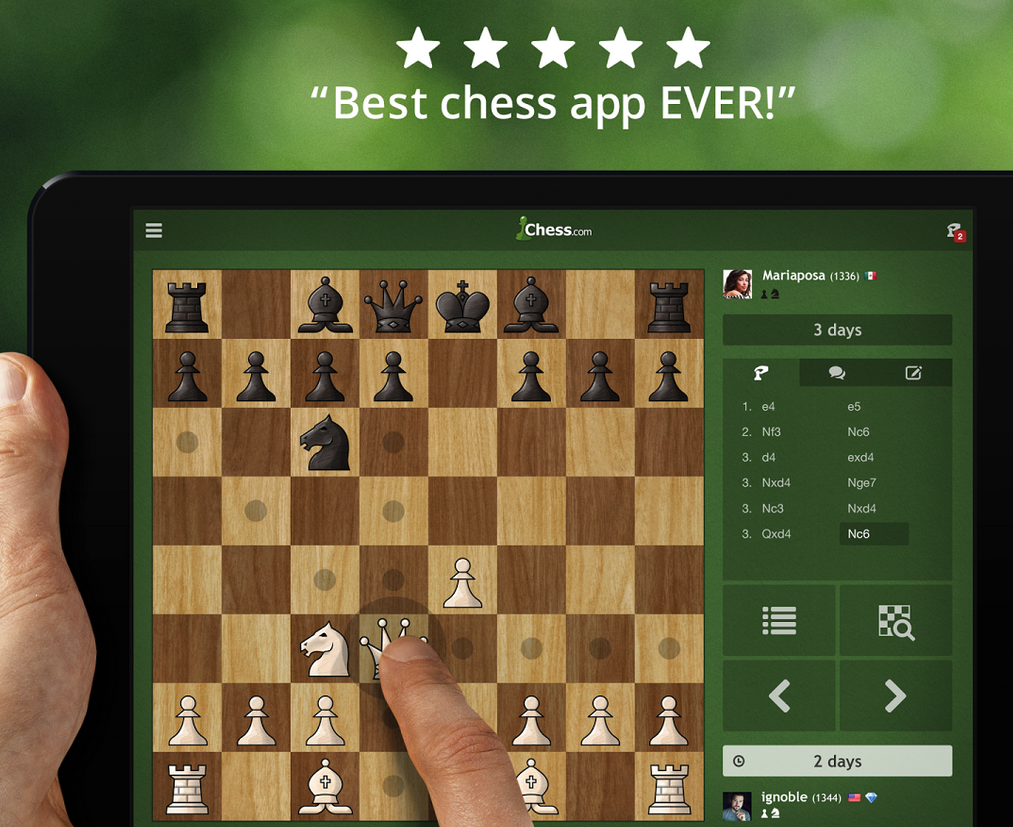
Chess
Business: Software made to assist
users in business, such as, accounting,
finances, and HR

Dynamics 365

Dropbox

BambooHR

HubSpot
Education/Reference: Made for students
and for research
Desmos
Google Translate

Swift
Britannica
A group of software whose purpose is to perform specific tasks the user wants
System Application
3 Categories
Operating system: A large piece of software that is responsible how other programs interact with pieces of hardware, usually through device drivers
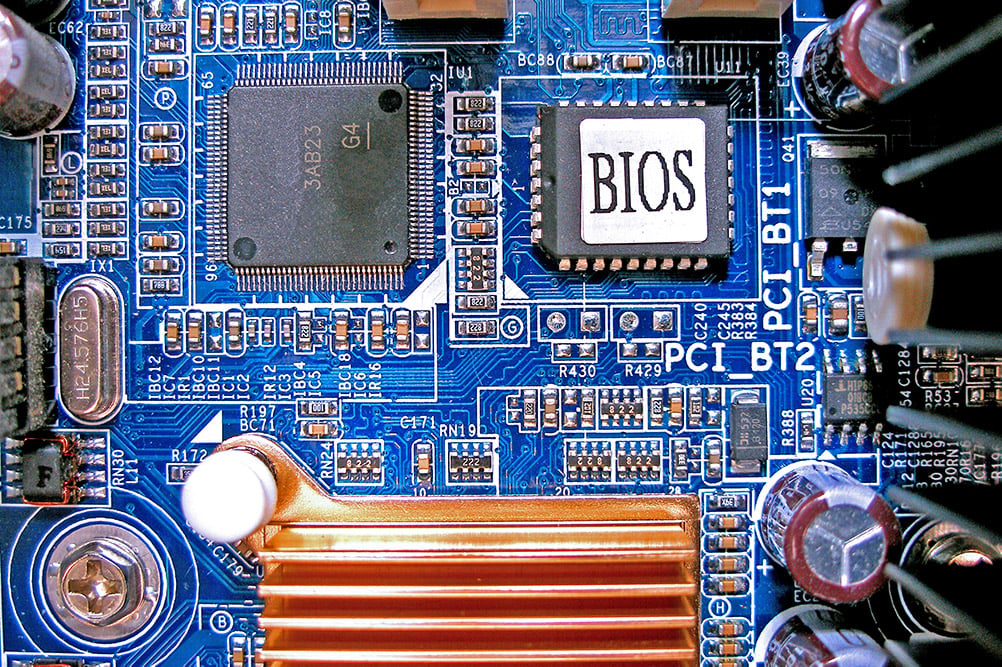
BIOS: A type of driver that manages the basic input and output of a computer.
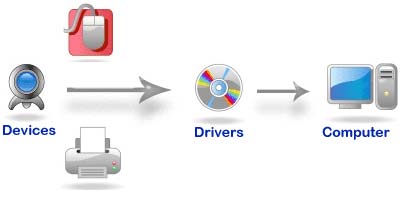
Device Drivers: Small programs that provide program interfaces to determines how the other programs interact with hardware
What is it? It is responsible for communication between hardware and other software
^