Computer software
Application Software
Application software is a group of software who's job is to perform user task's. Typically they are very specialized in
what they do. These tasks can range from listening to music, playing video games or creating a database.
Productivity

Google Docs
Word processor that allows you to edit
and create documents.
Google Spreadsheet
Software that allows you to create spreadsheets.
GIMP
Open-source graphics editor used for editing images and free form drawing.

Photoshop
Raster graphics editor used for digital art professionally.
Entertainment

Minecraft
Sandbox type of game where players are given the goal of exploring, creating and surviving.
Spotify
Spotify is a digital music, podcast and video service that provides music from and content from creators all over the world.
VLC
VLC is a free and open-source, portable, cross-platform media player software and streaming media server.

Roblox
Roblox is a video game platform that allows people to play a variety of games, create games and chat with players online.
Business
Dropbox
Dropbox is software that offers cloud storage, file synchronization, personal cloud, and client software.

Asana
Asana is a platform that allows business and teams to manage their work from a web or mobile platform.

Inflow
Inflow is a software that allows users to manage their business by buying and restocking orders.

Dynamics 365
Microsoft Dynamics 365 is a cloud-based business applications platform that combines components of customer relationship management and enterprise resource planning with the aid of AI.
Subtopic
Education/Reference
Desmos
Desmos is a graphing calculator that can plot a variety of different equations from lines to parabolas to functions.

Encyclopedia Britannica
Software that holds the worlds oldest published Encyclopedia.

Scratch
Scratch is a coding platform that uses blocks and visuals to try to teach children how to code.

Geometer's Sketchpad
Geometer is an interactive geometry software that allows people to explore algebra, calculus and much more mathematics.
Development Software
Development software is software that allows people to create new code or fix old code
Compiler
A program that is used to translate code from one language (say C, Java or Python) into a language the computer itself understands . The result is usually a file that can be executed or run on the target system.

Interpreter
Executes commands. In fact, an interpreter takes a program one line at a time and executes each line as it arrives.

Integrated Development Environment
An interface, usually graphical, that combines an editor window used to write code, an interpreter and a compiler into one package. An IDE also allows you to "debug" or execute a program one line at a time while giving access to all of the program's memory.

System application
System application is software that is responsible for the job of communicating the hardware with other software.
Operating systems
Operating Systems: A large piece of software that is responsible for managing how other programs interact with various pieces of hardware.

Device drivers
Small programs that provide an Application Program Interface which determines how other programs can interact with hardware.

BIOS
A type of driver that controls how your computer operates (start-up, hardware communication/interaction)

Malware
Malicious software or known as malware is any software that exists to be disruptive.
Trojan
Program or file that says it's one thing (like a video or game) and is really something else (like a virus or spyware)
Bitfrost, a remote access Trojan that infected Windows clients by changing, creating and altering components.
Viruses
Spreads by copying itself. Can affect any type of computer functionality by changing existing programs
Mydoom scraped addresses from infected machines, then sent copies of itself to those addresses.
Adware/spyware
Collects information about the user and changes web searches or traffic to other sites
Dollarrevenue would browser toolbar on the affected computer to track the internet searches performed on the computer. Alongside with that it would show deceptive ads.

Subtopic
Worms
Like a virus except it doesn't need to change existing programs to work
This worm known as ILOVEYOU sent copies of itself to every email address in the infected machine’s contact list.

Backdoors
Any way around a security measure without authorization.
This backdoor known as ShadowPad based in management applications of South Korea- and U.S.-based NetSarang has the ability to download and install malware and spoof data.

Timeline of computer viruses

The creeper virus created in 1971 designed by Bob Thomas. It was an experimental virus designed to to see if a self-replicating program was possible it did not cause a major impact nationally/internationally but would cause system damage to the computer when experimented with.

The Elk Cloner virus designed by Rich Skrenta, a 15-year-old in 1982. Elk Cloner infected Apple II computers via infected floppy disks, and would display a poem after every 50th boot. It infected millions of computers but it did not negatively impact. It's intent was to be a prank played on friends.

Created in 1987 by Basit and Amjad Farooq Alvi, in Pakistan. The virus would infect executable files on DOS-based computers and delete any program that was run on Friday the 13th. It quickly spread worldwide and caused significant damage to businesses and government agencies.

Robert Tappan Morris, a graduate student at Cornell University, createda worm to estimate the size of the internet in 1988. The worm took advantage of several flaws in the UNIX operating system, causing significant network slowdowns and crashes. The Morris Worm is estimated to have caused $100,000 in damage.

This virus was named after the famous artist by a group of hackers in the Netherlands in 1991. The virus was programmed to go off on Michelangelo's birthday (March 6) and overwrite the first 100 sectors of a hard disc, rendering it unusable. It caused about $10 million in damages worldwide.
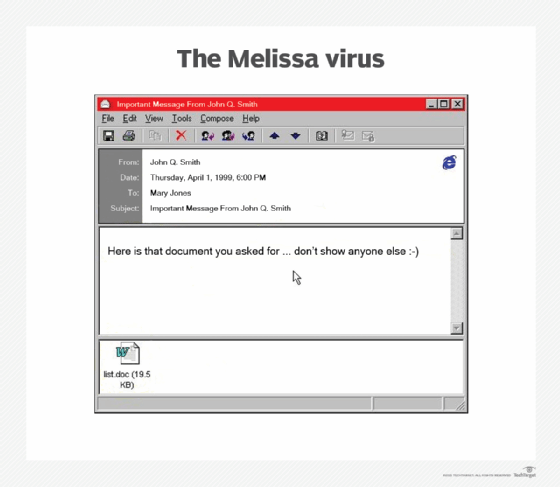
David L. Smith, a computer programmer from New Jersey, created this virus in 1999. The virus was distributed via email and infected Microsoft Word documents. When infected, the virus would send itself to the victim's first 50 contacts in their address book. Melissa's intent was to wreak havoc on businesses.
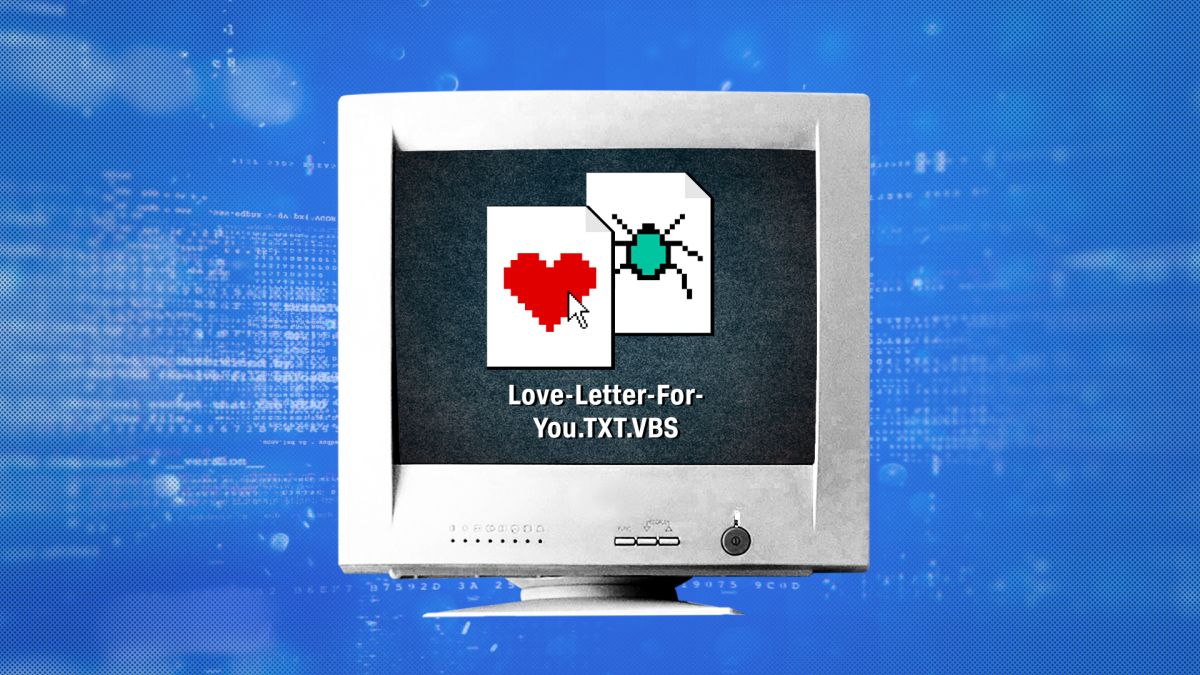
The ILOVEYOU virus was created in the year 2000 by two Filipino computer programmers, Onel de Guzman and Reonel Ramones. The virus was distributed via email with the subject line "ILOVEYOU." When the virus is activated, it overwrites files on the victim's computer and sends itself to everyone in the victim's address book. The virus is estimated to have caused $10 billion in damage and affected millions of computers around the world.
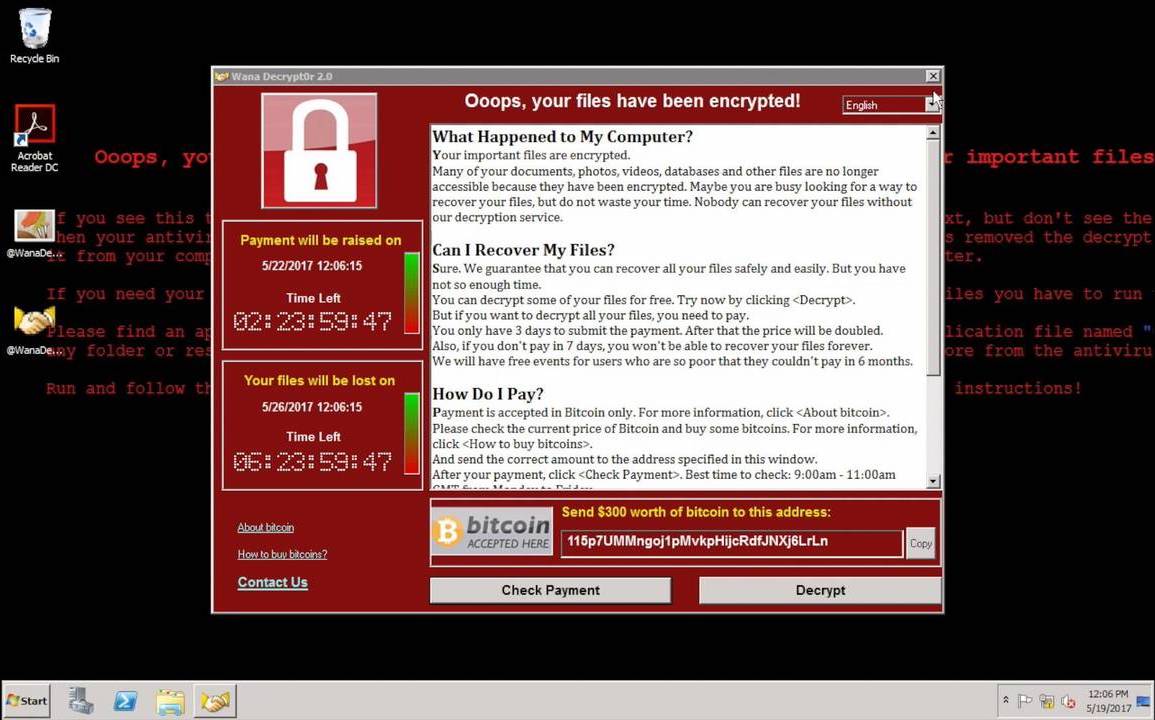
WannaCry Ransomware (2017): The Lazarus Group, a group of North Korean hackers, created this ransomware virus in 2017. It took advantage of a flaw in Microsoft Windows and quickly spread throughout networks all over the world. Once infected, the virus encrypts the victim's files and demands a Bitcoin ransom to unlock them. WannaCry caused widespread disruption, affecting organisations such as the NHS in the United Kingdom and FedEx in the United States. The virus is estimated to have cost more than $4 billion in damages.
Five ways of avoiding or preventing computer viruses

Install antivirus or anti-malware software. A good example could be malwarebytes a free and reliable antivirus software that scans your computer for.
Run antivirus scans regularly, many computers that come with windows have windows defender already included that can regularly perform scans. For computers that don't they can regularly scan with antivirus software.

Keep your operating system up to date, whether it be Linux or Windows developers are regularly patching and upgrading security in operator systems.

Think before you click, you should always avoid sketchy websites or websites you do not trust, sometimes you can even run links through antivirus software such as VirusTotal will show if a URL has any discrepancy.
Don’t use unsecured Wi-Fi, often times wifi that is publically available have no security measures and can easily be broken into. Examples could be wifi at free cafes or libraries.