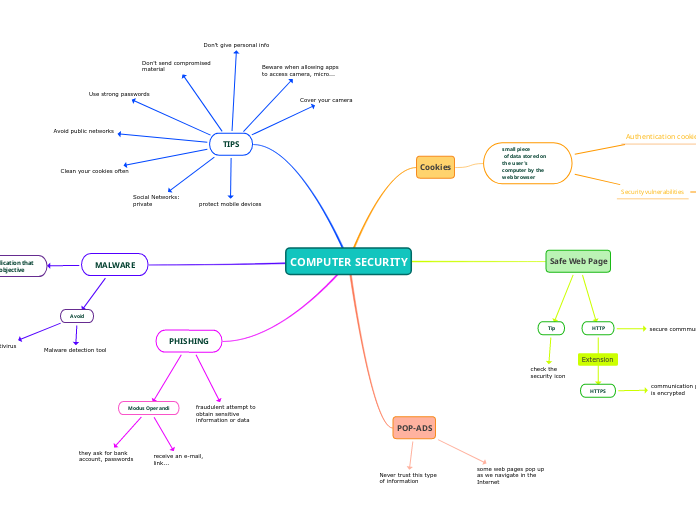
COMPUTER SECURITY
PHISHING
fraudulent attempt to
obtain sensitive
information or data
Modus Operandi
they ask for bank
account, passwords
receive an e-mail,
link...
MALWARE
Avoid
Malware detection tool
Antivirus
program or application that
has a malicious objective
obtain personal data
& money
TIPS
Don't give personal info
Cover your camera
protect mobile devices
Social Networks:
private
Clean your cookies often
Avoid public networks
Use strong passwords
Don't send compromised
material
Beware when allowing apps
to access camera, micro...
POP-ADS
Never trust this type
of information
some web pages pop up
as we navigate in the
Internet
Safe Web Page
HTTP
secure commmunication
HTTPS
communication protocol
is encrypted
Tip
check the
security icon
Cookies
small piece
of data stored on the user's
computer by the web browser
Security vulnerabilities
read by an attacker
Authentication cookies
remember pieces
of information
to know whether the user
is logged in or not