by Juan Diego Renal Florez 3 years ago
218
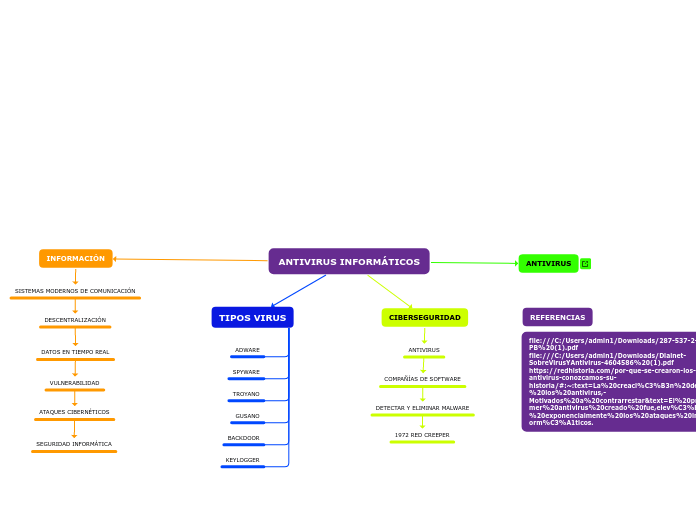
ANTIVIRUS INFORMÁTICOS
by Juan Diego Renal Florez 3 years ago
218

More like this
DETECTAR Y ELIMINAR MALWARE
1972 RED CREEPER
DATOS EN TIEMPO REAL
VULNERABILIDAD
ATAQUES CIBERNÉTICOS
SEGURIDAD INFORMÁTICA